Friend gave us a heads up on a discord server i’m in that there’s a new scam on Steam, if you get a playtest invite/message do not click on it

It wasn´t a real hacker attack. They simply co-opted an employee who was unhappy with his salary, gave him about $3,000.00 and the poor guy used his own credentials to execute commands on the system.
Also - the little box that holds consecrated hosts.
TIL, thanks.
The Central Bank is about to release a virtual currency called Digital Real or just Drex. It won´t be a cryptocurrency, as it will be backed by the Central Bank of Brazil and will have a value that corresponds to that of the physical money currently issued.
Of course, this created a bit of a buzz in the tinfoil hat community, who believe that this time it’s the implementation of the cipher 666, for real. Unfortunately, not every American conspiracy theory gains traction here, as cultural transposition is not automatic.

[…]
Twitter co-founder Jack Dorsey’s latest idea for a “secure” comms network that doesn’t rely on a traditional mobile phone or Wi-Fi network, called Bitchat, has run into a few Bluetooth problems of its own.
[…]
Alex Radocea, who’s worked on security for Apple, Spotify, and CrowdStrike, spotted basic security errors in what he politely called BitChat’s “decorative” authentication systems that would allow an attacker to access contact logs and possibly even messages sent with the system. He suggested BitChat’s developers used AI to code the app.
“There’s essentially no trust/auth built in today. So I would not really think about this as a secure messenger,” he advised.
[…]
How does your phone know so many private details? How thousands of apps are exploiting mysterious indoor location tracking
A little technical, but this type of attack (UEFI-based) is occurring more and more frequently.
Gigabyte published a (back-dated!) security notice about this that includes a list of the motherboard chipsets that are affected by this.
Here’s the CERT/CC note about this, which includes a bit more information about each vulnerability, along with a list of 23 motherboard vendors and an indication of which ones (other than Gigabyte) may be affected.
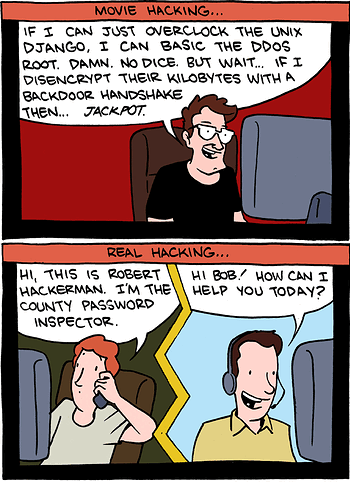
It’s certainly so much easier to do attack vectors through social engineering or phishing
Most of the computer stuff is satirical (despite using some actual state-of-the-art hardware), but the social engineering is top notch.
Kevin Mitnick couldn’t hack his way out of a paper bag, but boy was he convincing over the phone.